Apache Server Hardening for Ubuntu 18.04 LTS

When people taking about building a web server. commonly people will used Apache Web Server. In the version of Ubuntu 18.04 Server edition, it has set all the basic security setting in place as below :
Hide Apache Version and Operating System and only show Server: Apache in the Header
ServerTokens Prod and ServerSignature off parameter in /etc/apache2/conf-avaliable/security.conf file.
TRACE HTTP Request will be Disable to prevent Hackers easily capture the cookies information
TraceEnable off parameter in /etc/apache2/apache2.conf file.
There have some security area where it will not set as default due to the Web Application Design perquisite. Some application needed to list web directory and FollowSymLinks to download some file in the servers. Some also needed to lower down the security setting to minimize the impact of the Web Application Design. Like the Feature Policy, Referrer Policy and Content Security Policy. For me those are the options are recommended to deploy in the Header. If you not sure how your Web Application Policy Design, it is challenge for you to do this configuration.
As recommended to put the Header parameters in the
Required to deploy this Security parameters to prevent hackers to steal and malicious script where it be access any cookies, session tokens, or other sensitive information retained by the browser.
Header set Set-Cookie HttpOnly;Secure
Header always append X-Frame-Options SAMEORIGIN
Header set Strict-Transport-Security "max-age=3153600"
Header set X-Content-Type-Options nosniff
Header set X-XSS-Protection: "1; mode=block"
recommended to deploy these policies if you understand your Web Application Security Design
Header set Referrer-Policy "no-referrer-when-downgrade"
Header always set Feature-Policy "microphone 'none'; payment 'none'; sync-xhr 'self' https://www.your-web.site"
Header set Content-Security-Policy "default-src 'self';"
If you not sure where to deploy this parameters below is the screen caputure to guide you.
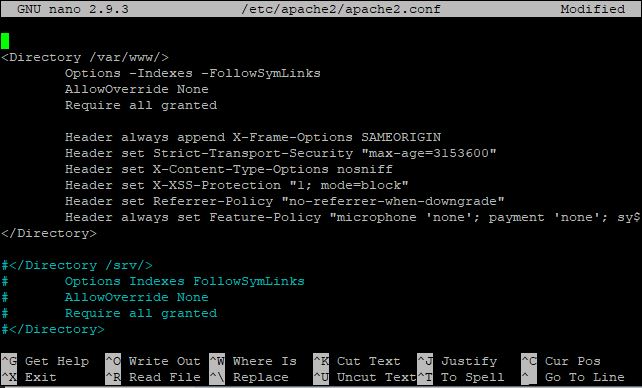
Save the file and restart the apache service.
sudo systemctl restart apache2
Hide Apache Version and Operating System and only show Server: Apache in the Header
ServerTokens Prod and ServerSignature off parameter in /etc/apache2/conf-avaliable/security.conf file.
TRACE HTTP Request will be Disable to prevent Hackers easily capture the cookies information
TraceEnable off parameter in /etc/apache2/apache2.conf file.
There have some security area where it will not set as default due to the Web Application Design perquisite. Some application needed to list web directory and FollowSymLinks to download some file in the servers. Some also needed to lower down the security setting to minimize the impact of the Web Application Design. Like the Feature Policy, Referrer Policy and Content Security Policy. For me those are the options are recommended to deploy in the Header. If you not sure how your Web Application Policy Design, it is challenge for you to do this configuration.
As recommended to put the Header parameters in the
Required to deploy this Security parameters to prevent hackers to steal and malicious script where it be access any cookies, session tokens, or other sensitive information retained by the browser.
Header set Set-Cookie HttpOnly;Secure
Header always append X-Frame-Options SAMEORIGIN
Header set Strict-Transport-Security "max-age=3153600"
Header set X-Content-Type-Options nosniff
Header set X-XSS-Protection: "1; mode=block"
recommended to deploy these policies if you understand your Web Application Security Design
Header set Referrer-Policy "no-referrer-when-downgrade"
Header always set Feature-Policy "microphone 'none'; payment 'none'; sync-xhr 'self' https://www.your-web.site"
Header set Content-Security-Policy "default-src 'self';"
If you not sure where to deploy this parameters below is the screen caputure to guide you.

Save the file and restart the apache service.
sudo systemctl restart apache2
























